Stack Canaries
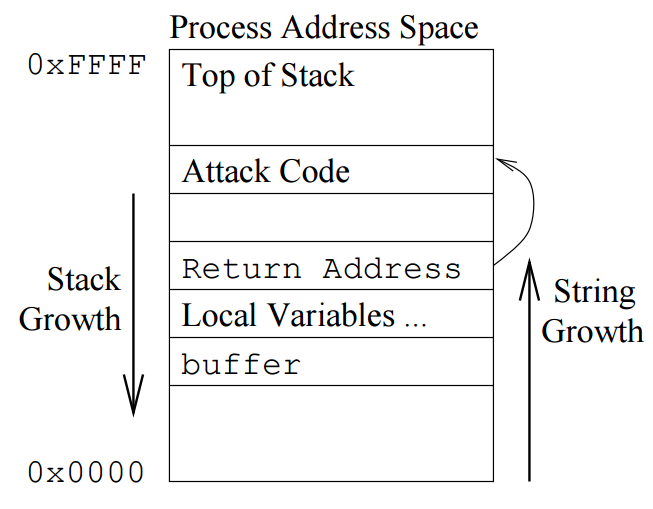
One of the most important buffer overflow attacks is the first Internet worm, written by Robert Morris Jr. in 1988. It modified the return address on the stack, injected malicious code, then it controlled the system. (See figure 1-1 Stack Smashing Buffer Overflow Attack)
Figure 1-1 Stack Smashing Buffer Overflow Attack (Source: [StackCheck][1] )
In 1999, StackCheck was introduced to prevent buffer overflow attack on a stack.[StackCheck][1]>
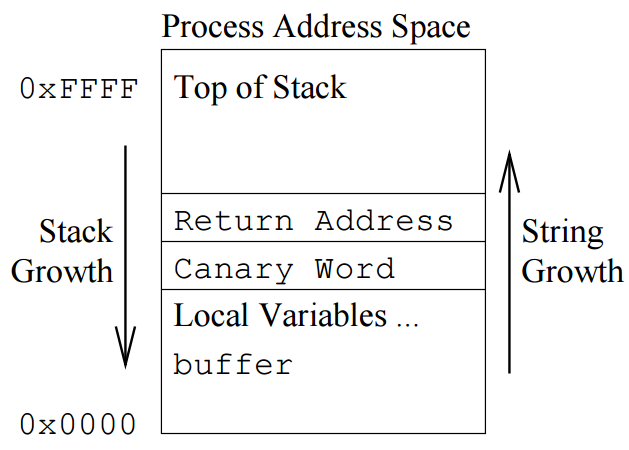
When the program makes a function call, it puts a random digital canary on top of the return address on the stack. When the function returns, the program checks if the canary data is modified. If it is modified, there must be something wrong and a special failure reporting function is invoked before the program returns back to the function address on the stack. (See figure 1-2 Canary Word Next to Return Address)
Figure 1-2 Canary Word Next to Return Address (Source: [StackCheck][1])
Stack canary is a software feature. It is supported by most compilers.
[1] [StackCheck] StackGuard: Automatic Adaptive Detection and Prevention of Buffer-Overflow Attacks. Cowan, C., Pu, C., Maier, D., Hintongif, H., Walpole, J., Bakke, P., Beattie, S., Grier, A., Wagle, P., Zhang, Q. Proceedings of the 7th USENIX Security Symposium (January 1998)
Last updated